Do You Know What You Have On Your Network And What It Is Doing?
Let us help you identify and secure these components whiles maintaining essential functionality.








Choose the right solution for you.
(+233) 30 285 2909
The Growing Cyber Threat Landscape
Why Choose Us
Our comprehensive Cyberbersecurity solutions designed to keep your data safe.
We begin by understanding your business environment, infrastructure, and security needs.
Continuous validation of security controls and implementations ensures your defenses remain effective.
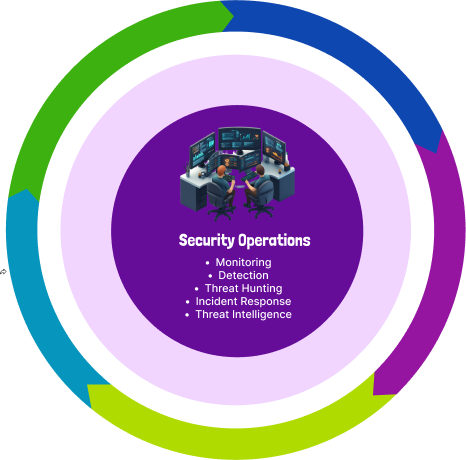
Monitoring
Detection
Threat Hunting
Incident Response
Threat Intelligence
Through detailed analysis, we identify potential threats, vulnerabilities, and their potential impact on your business.
Our experts conduct thorough technical evaluations including penetration testing, vulnerability scanning, and security architecture review.
Latest Project
Powerful defense strategies for your company’s digital security.

ExeCutioner

DMappedInjector

SQLinkedCodeExec
