Our Services
Guarding your digital assets with industry-leading cyber expertise.

Our Services
Security Solutions That Scale With Your Business
85% of vulnerabilities detected before exploitation
99.9% uptime with continuous monitoring
15-minute average incident response time
What we offer
Keeping your sensitive information secure and always protected.
Comprehensive security assessments that simulate real-world attacks to identify vulnerabilities in your systems before malicious actors do.
Secure your cloud infrastructure. Includes configuration reviews, access management, and continuous security monitoring
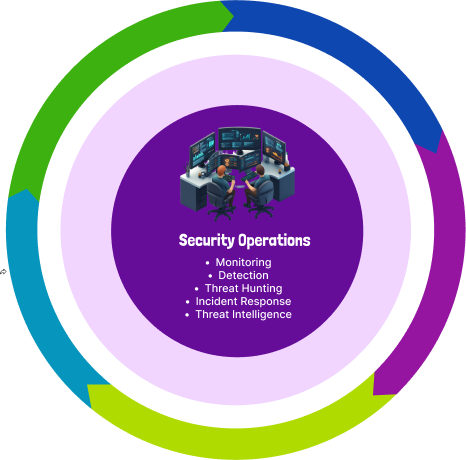
24/7 security operations center providing continuous monitoring, threat detection, incident response, and security management
Expert guidance on security strategy, compliance, risk assessment, and building robust security programs tailored to your business needs.
Rapid response team ready to handle security breaches, ransomware attacks, and other cyber incidents. Including forensics and recovery services
Comprehensive training programs to transform employees into your strongest security asset. Includes phishing simulations and security best practices.
Why Choose Us
Our comprehensive Cyberbersecurity solutions designed to keep your data safe.
We begin by understanding your business environment, infrastructure, and security needs.
Continuous validation of security controls and implementations ensures your defenses remain effective.
Monitoring
Detection
Threat Hunting
Incident Response
Threat Intelligence
Through detailed analysis, we identify potential threats, vulnerabilities, and their potential impact on your business.
Our experts conduct thorough technical evaluations including penetration testing, vulnerability scanning, and security architecture review.
