A suspicious activity appears on your network.
Something is off. Logs don’t look right. Alerts start firing. Maybe an attacker is already moving laterally or worse, you’re discovering the compromise far too late.
In that moment, what do you do?
When we look at organizations that respond to real-world emergencies such as the police, military, fire services, one thing stands out clearly: they train constantly. They run drills. They simulate incidents. They rehearse decision-making under pressure so that when the real thing happens, response becomes instinctive.
Now let’s be honest.
Do we treat cybersecurity incident response the same way?
Most organizations say they have an incident response plan. Fewer test it regularly. Even fewer actively train responders in realistic, repeatable scenarios that sharpen judgment, coordination, and technical decision-making.
And that’s a problem.
The Gap in Cyber Incident Response Training
Incident response is not just about knowing tools or frameworks. It’s about thinking clearly under pressure, asking the right questions, prioritizing actions, and understanding consequences in real time.
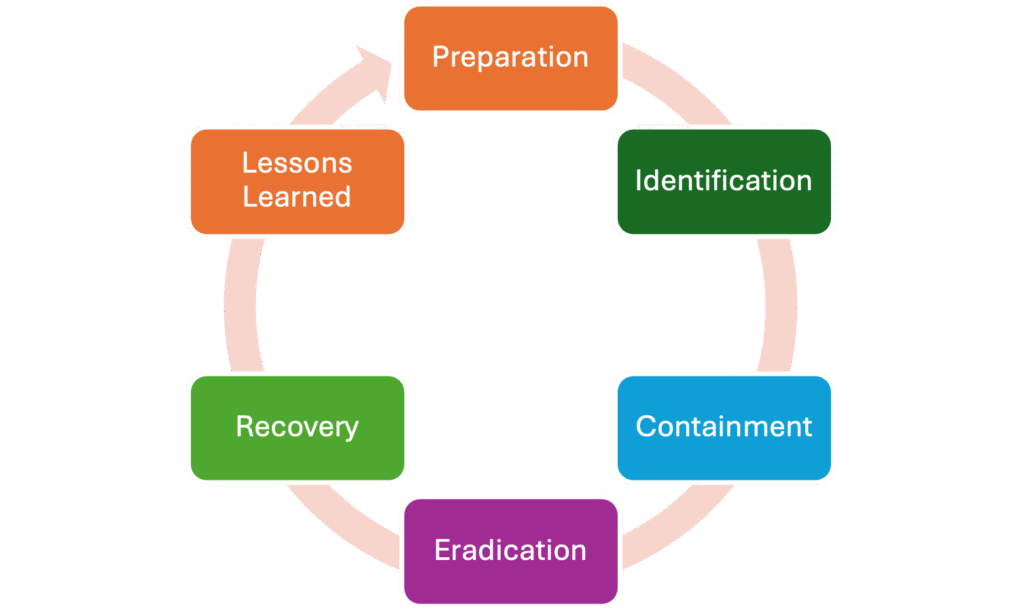
This aligns closely with the SANS Incident Response framework, which breaks effective response into structured phases: preparation; identification; containment; eradication; recovery; and lessons learned. On paper, the process is clear. In practice, however, moving through these phases during a live incident is rarely linear, calm, or predictable.
That’s where many teams struggle, not with knowing what the phases are, but with knowing how to apply them under real-world constraints: incomplete information, time pressure, competing priorities, and high-stakes decisions.
This is where Backdoors & Breaches, a tabletop incident response game developed by Black Hills Security, shines.
The game simulates real-world cyber incidents and forces players to think like responders. You’re presented with scenarios, limited information, and evolving conditions. You must decide what to do next who to involve, what to investigate, what actions to take and live with the outcomes.
It’s brilliant.
But I ran into a problem.
A Great Game… With One Big Limitation
As good as Backdoors & Breaches is, it assumes something many practitioners don’t always have: a group of people ready to play.
At the time, I wasn’t actively working in a SOC. I didn’t have a team on standby to run tabletop exercises whenever I wanted. Yet I really wanted to learn the game deeply, not just understand the rules, but internalize the thinking behind effective incident response.
I wanted to play:
- On my own
- At any time
- As often as I needed
So I asked myself a simple question:
What if I could play this game solo?
Turning AI Into an Incident Master
That question led to an idea and eventually, a solution.
I built a solo version of Backdoors & Breaches, where a large language model acts as the Incident Master. Instead of a human facilitator, the AI drives the scenario: presenting events, responding to decisions, escalating incidents, and revealing consequences based on player actions.
This changed everything.
Suddenly, I could:
- Practice incident response repeatedly
- Explore different decision paths
- Learn from mistakes without pressure
- Build intuition over time
It wasn’t just convenient it was transformational.
AI as a Force Multiplier for Cybersecurity Training
What started as a personal learning experiment quickly became something bigger.
I shared the project with the community, and the response was overwhelming. Practitioners immediately saw the value: a way to stay sharp, rehearse incidents, and build confidence—without needing a full team or scheduled sessions.
Today, the project has 25 stars on GitHub and is actively being improved with new features, scenarios, and refinements. It’s open source, community-driven, and focused on one core goal:
Helping defenders know what to do when it actually matters.
This is one of the most practical ways AI can be integrated into cybersecurity education—not as a replacement for humans, but as a training partner that never gets tired, never runs out of scenarios, and is always available.
Staying Ready Before the Incident Hits
Breaches don’t wait until you’re prepared.
The question isn’t if something will go wrong, but whether your responders will be ready when it does.
If we expect cyber defenders to perform under pressure, we must give them the same thing emergency responders have relied on for decades:
Realistic drills. Repetition. Muscle memory.
Explore the Project
If this resonates with you—whether you’re a SOC analyst, incident responder, trainer, or simply curious about practical ways to improve cyber readiness—you can explore the project here:
🔗 Backdoors & Breaches – SOC Invader (Solo Edition)
https://github.com/0xJaeg3r/backdoorsandbreaches-socinvader
Feel free to try it, break it, suggest improvements, or contribute. The goal is simple: help the community stay sharp, stay ready, and respond better when the inevitable incident arrives.

